Why
Because software as it is currently written is impossible to secure. The “poke and patch” methodology does nothing to prevent the introduction of software defects (bugs) and can actually resurrect old ones via regressions or introduce entirely new issues.
If debugging is the process of removing software bugs, then programming must be the process of putting them in.
— Edsger Dijkstra
Increasing Frequency, Severity, and Scope
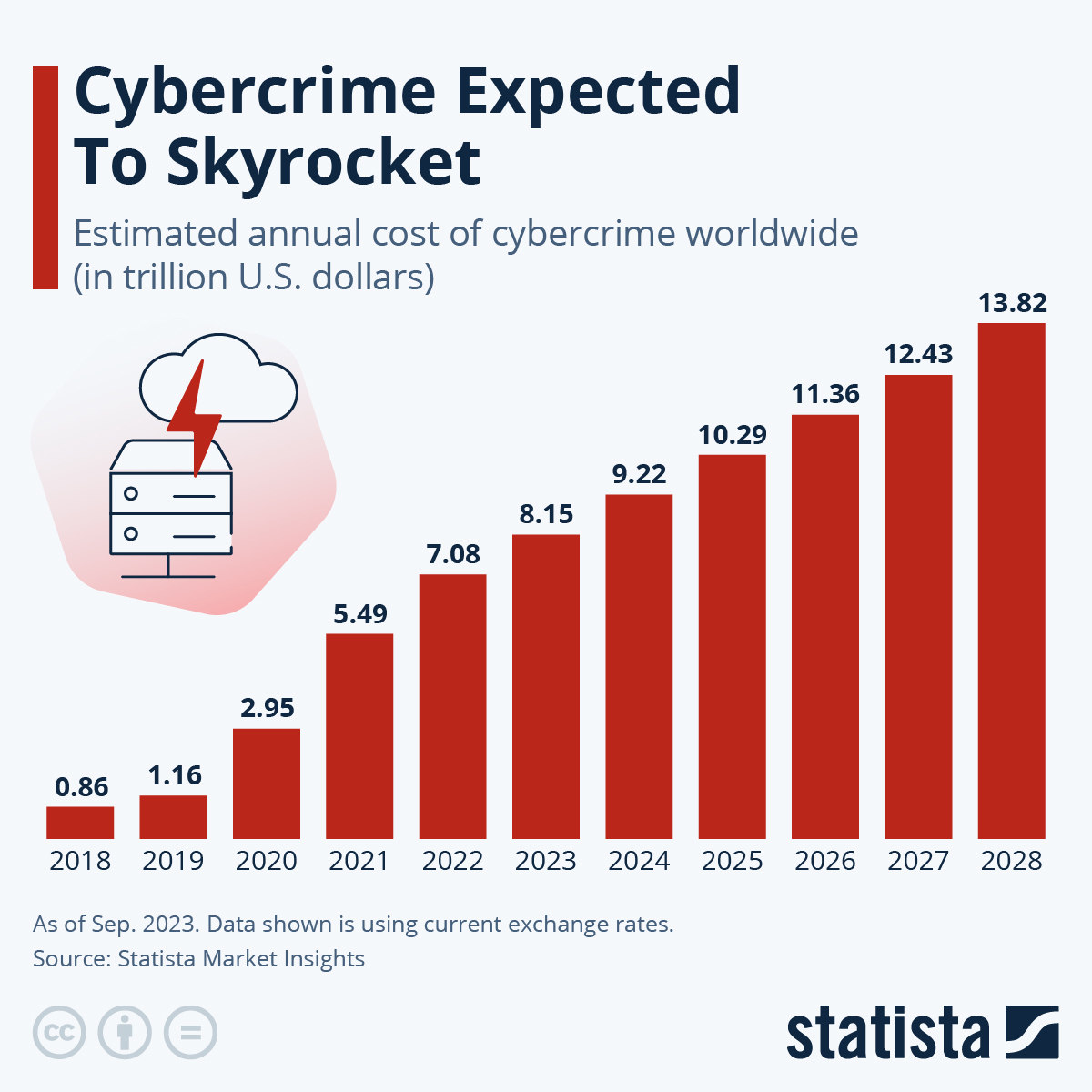
The frequency, severity, and scope of attacks continues to increase at an exponential rate. Obviously, something is wrong as today’s approaches are utterly failing to mitigate these threats. Some “solutions” are actually becoming threats themselves e.g. CrowdStrike and SolarWinds.
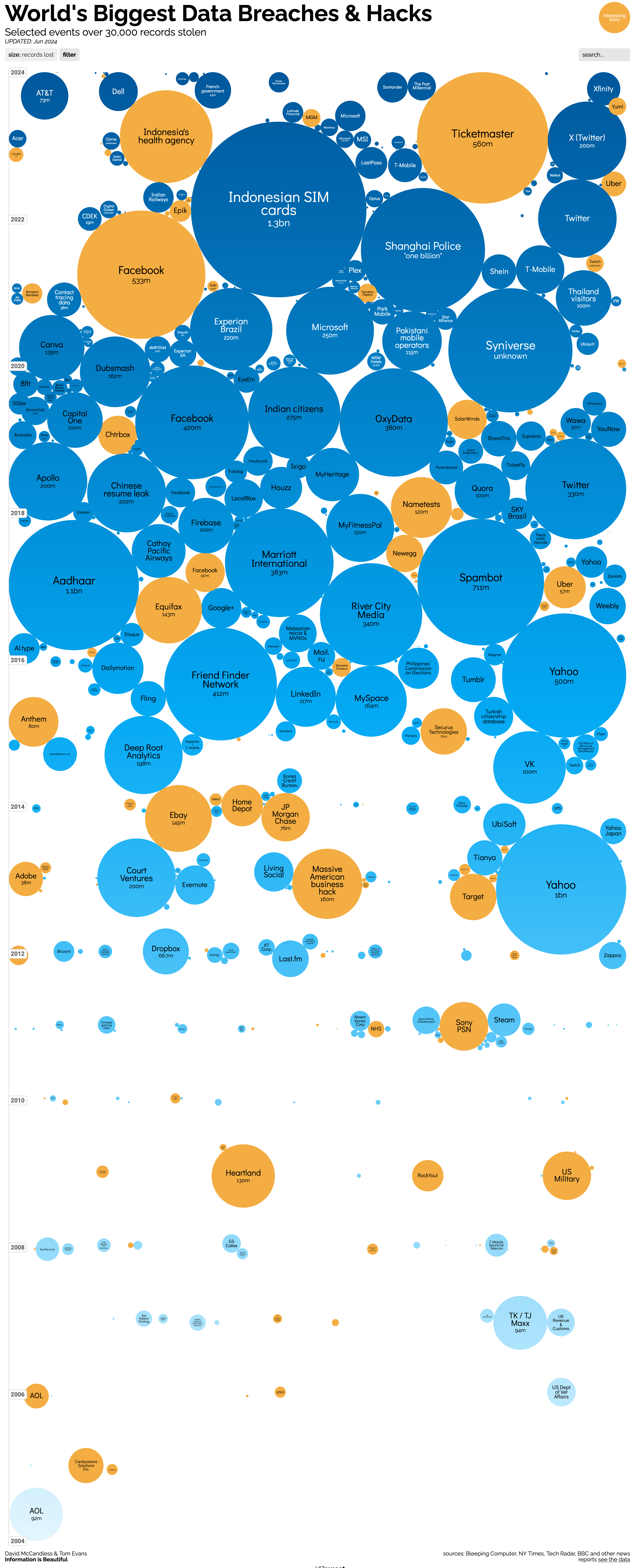
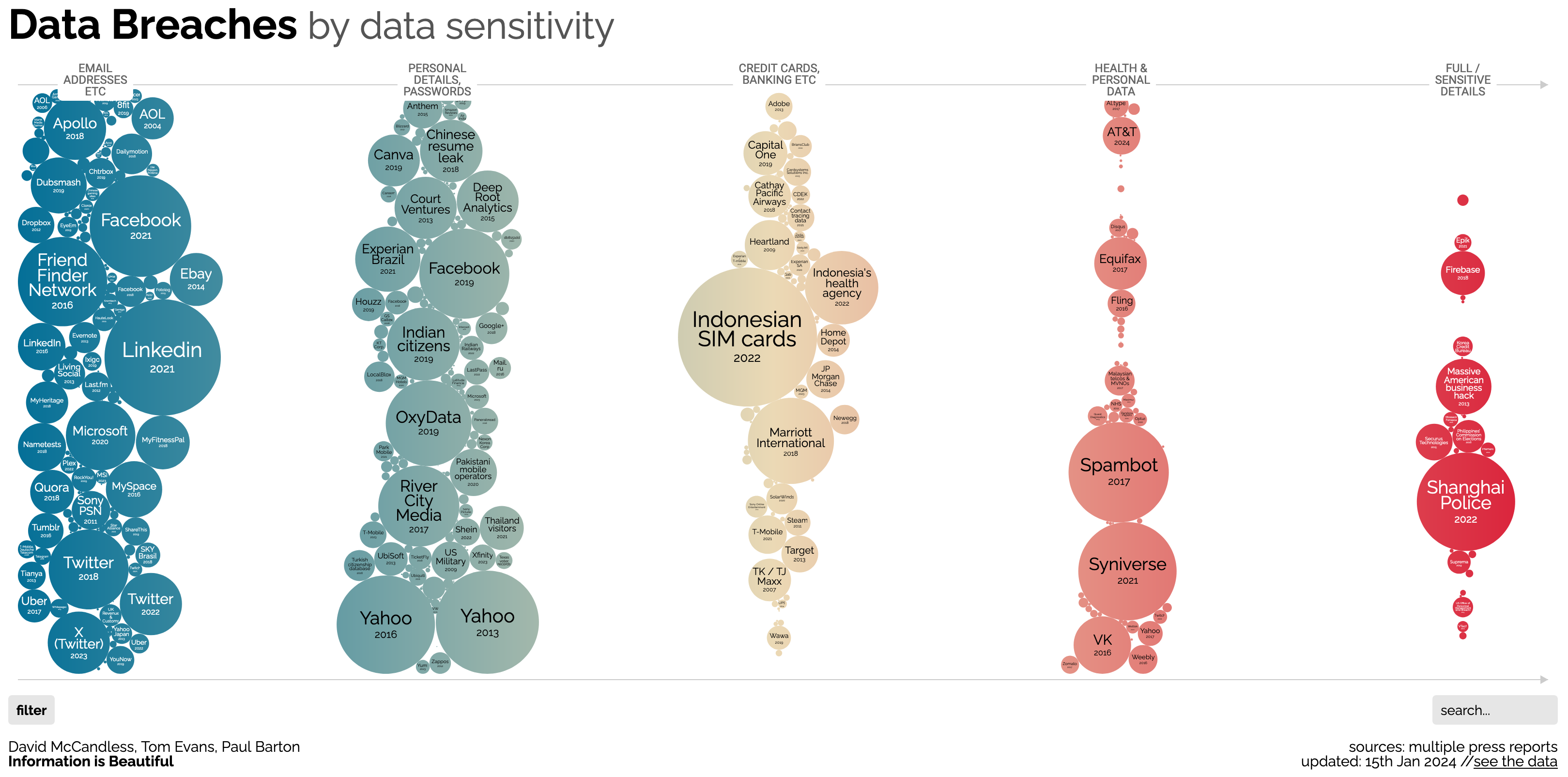
The following chart shows breaches sized by records lost and ordered from most recent at the top to least recent at the bottom. It’s clear that the current industry practices insufficient and the state of cybersecuriy is trending in the wrong direction.
Rising Costs
According to the Cost of Poor Software Quality in the U.S.: A 2022 Report by CISQ:
Our 2022 update report estimates that the cost of poor software quality in the US has grown to at least $2.41 trillion, but not in similar proportions as seen in 2020. The accumulated software Technical Debt (TD) has grown to ~$1.52 trillion.
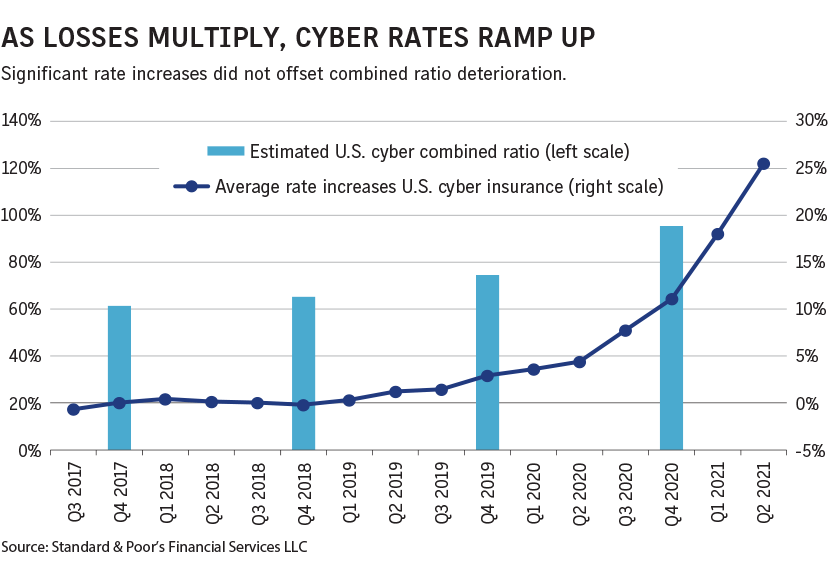
While businesses have been content to address the problem by purchasing insurance, as the rates of software defects and thus cyberattacks continue to rise that is unlikely to remain tenable:
- The cost of cyber insurance increased 32% last year (2021)
- Insurers run from ransomware cover as losses mount
- French cyber insurance provider to stop covering ransomware
- Cyber attacks set to become ‘uninsurable’, says Zurich chief
Coming Regulation
The Cybersecurity and Infrastructure Security Agency (CISA) has realized that their mission of securing the nation’s software and infrastructure is currently impossible. Under the direction of Jen Easterly they have announced the Secure by Design initiative to finally demand that software be held to the same standards as other engineering professions.
How do we convince people that in programming simplicity and clarity - in short: what mathematicians call elegance - are not a dispensable luxury, but a crucial matter that decides between success and failure?
—Edsger Dijkstra
Economic Collapse of Computing
At some point, the money lost due to cybersecurity incidents and poor quality software will outpace the revenue that can be made by various industries. When this happens we’ll see an economic collapse due to the inability of any business in a given sector to make money if computers are involved.